
13 Strategies to Make Your Cybersecurity Failproof in 2022
Skilled hackers can easily access your system and steal precious business information. Upgrading your cybersecurity can help address this problem.
Taking your cybersecurity seriously is critical. In fact, it’s so important today that there are laws and statutes in place to encourage the adoption of cybersecurity best practices. Otherwise, you leave the door open for criminals to compromise your business’s data, privacy, and proprietary information as well as cause legal troubles.
Now, you might think that cybercriminals only target large companies due to more resources. But that’s not the case. Small businesses make attractive targets because they often don’t have the same protections in place.
Whether you’re a small or medium-sized organization, you have a large amount of sensitive data that hackers can utilize. If it ends up in the wrong hands, your reputation can be ruined, and you may lose access to invaluable information. Sixty percent of businesses that experience a data breach end up closing within 6 months.
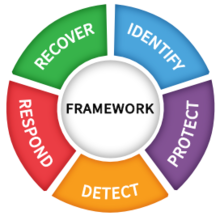
The good news is that every business leader can prevent this scenario. And the best way to do so is to take cybersecurity measures seriously and implement a cybersecurity plan following a recognized cybersecurity framework like the NIST CSF.
 This article will share the 13 most effective strategies for making your cybersecurity disaster-proof.
This article will share the 13 most effective strategies for making your cybersecurity disaster-proof.
THE 13 STRATEGIES
STRATEGY #1 – UPGRADE CLOUD SECURITY
Data cloud storage is cost-effective and convenient, but that doesn’t mean you should use just any platform.
Look for the most secure ones that prioritize safety features. OneDrive, DropBox, and Google are some of the more popular options that work to improve security routinely. Some alternative options include Icedrive, pCloud, and Sync.com.
STRATEGY #2 – SECURE EACH PART OF YOUR NETWORK
Mobile devices, computers, and laptops connected to your network can be ideal entry points for hackers. Safeguarding these devices with decisive authentication measures is a great way to prevent cyberattacks.
You can benefit from having strong Wi-Fi and device passwords. They limit access and help ensure only your team members can enter your system.
Here are a few guidelines for creating strong yet convenient passwords:
- Don’t go overboard while mixing letters, symbols, numbers, and upper-case characters. Instead, come up with something simpler, but it should still have a minimum of 12 characters.
- Choose something you can easily memorize but difficult for an attacker to guess. Quotes, lyrics, and song/movie titles are a good method for Wi-Fi passwords.
- Never leave your password hints publicly available.
- Reset your passwords whenever you forget them. In addition, change them once a year to keep things fresh.
- Whenever possible use biometrics and MFA to logon to devices.
- For more password best practices check out this webinar hosted by Nwaj Tech.
STRATEGY #3 – USE ANTI-FRAUD SERVICES FOR CARD PAYMENTS
Seek advice from banks or your payment processor on selecting trustworthy, validated, and anti-fraud services. Besides protecting your information, they can also shield the data of your clients to help preserve your reputation.
STRATEGY #4 – INCORPORATE ADDITIONAL SECURITY MEASURES
Regardless of the number of security measures, you should always consider adding more.
Antivirus protection is a must and is the most common tool to combat cyberattacks. It can block malware from compromising your devices and data. Look for programs from reliable providers and only use one antivirus app per device. Today’s generation of antimalware protection includes several options that use AI and check for anomalous behavior on your devices that could be an indicator of compromise.
Adding Zero Trust enforcement and next-generation security will vastly improve your business’s cybersecurity.
Investing in firewall protection is another great idea if you want to safeguard your business against hackers. They can screen out viruses and other harmful activities on the internet and determine the traffic that can enter your devices. Combined with intrusion detection you have a virtual guard at the gate of your business.
That said, Mac OS X and Windows devices have their own firewalls, named Mac Firewall and Windows Firewall, respectively. You should also consider investing in a network firewall to protect your business where it meets the internet.
Finally, don’t forget about using virtual private networks (VPNs). They can stop web browsers, software, and people from accessing your connection, keeping the data you send and receive anonymous.
STRATEGY #5 – DON’T IGNORE UPGRADES AND UPDATES
 Software updates are often ignored by busy business owners and employees. However, this can be a huge mistake since outdated systems are more susceptible to hacking.
Software updates are often ignored by busy business owners and employees. However, this can be a huge mistake since outdated systems are more susceptible to hacking.
To prevent this, regularly upgrade and update your devices and software. This closes security holes and makes it harder for the bad guys to hack their way in.
STRATEGY #6 – DEVELOP SOUND PROTOCOLS WITH YOUR CUSTOMERS AND SUPPLIERS
Securing your communication and data sharing with suppliers and new clients is also paramount. If possible, only use direct contact channels via trustworthy personnel. Moreover, insist on codewords to denote changes in payments, terms, and other key details.
To further lower the risk of data theft through suppliers and clients, vet each person before granting them access to your system.
Whenever a change is requested confirm the change with a decision-maker or person of authority at the business requesting the change. Only use pre-approved channels when communicating with your vendors.
STRATEGY #7 – BACK UP YOUR DATA
Ransomware attacks are a common form of hacking. It involves cybercriminals holding your business hostage by restricting your access to your data until they receive a ransom.
To eliminate this concern, store your company information on multiple platforms and networks. Backing up your data can prevent your organization from crumbling due to inaccessibility.
Having verified backup sets of your company’s data will help to avoid having to pay a large ransom to retrieve your data.
STRATEGY #8 – ONLY USE APPROVED DEVICES AND CONNECTIONS
Work From Home has become more popular than ever (thanks to COVID). Although it’s helped enterprises lower costs, it’s also increased security risks. In particular, your employees might be using their own devices or networks that aren’t secure. These are ideal gateways for thieves to steal your information.
You can address this problem by rolling out your company mobile devices and allowing your team members to only work from them.
There are alternative steps for businesses that cannot provide devices to their employees but they are less secure and require employee buy-in.
STRATEGY #9 – BUY SIMILAR DOMAINS
Purchasing similar domains is an effective way to boost your cybersecurity. It can lower the risk of receiving emails with malicious attachments from spoofed addresses and links to spoofed websites.
STRATEGY #10 – TRAIN YOUR TEAM
A huge number of cyberattacks take place because of employee ignorance. Some employees often click on suspicious emails and fall for phishing schemes or share their passwords without any second thoughts.
The weakest link to any cybersecurity plan is the human link. Train, educate, and inform your entire team on how to recognize and stop potential cyberattacks.
At Nwaj Tech we routinely train our client’s teams and the business community to recognize potential cyberattacks and scams.
Set up phishing campaigns and simulations so you can prepare your team for potential security breaches.
STRATEGY #11 – RESTRICT EMPLOYEE ACCESS
Not all cyberattacks originate from outside your company – they can also come from within.
To reduce the damage someone from your enterprise can inflict with hacking, restrict employee access to only some sections of your system.
Using the theory of least privilege means only giving your employees enough access to do their assigned job, and nothing more. This can be accomplished using clearly defined roles.
 STRATEGY #12 – FOSTER A CULTURE OF SECURITY IN YOUR WORKPLACE
STRATEGY #12 – FOSTER A CULTURE OF SECURITY IN YOUR WORKPLACE
Cyber security should be the number one priority in all your departments and not just your IT provider. With everyone working together to shield their workplace from attacks, you’re much more likely to preserve your data.
At Nwaj Tech we believe customer service is not a department, but a culture. We also firmly believe that cybersecurity is EVERYONE’s priority, not just the technology team. This is accomplished through a culture that empowers employees to learn, and respond appropriately to potential threats.
Create a culture to defeat the bad guys.
STRATEGY #13 – REGULARLY CHECK FOR VULNERABILITIES
You don’t want to be idle after implementing all these defense mechanisms. Instead, conduct regular risk assessments and audits to identify weaknesses in your business’s physical cybersecurity. Doing so can help ensure that you patch up your vulnerabilities and upgrade your systems as appropriate.
Risk assessments should be completed at least yearly, more often if there are changes to the environment. You cannot understand all the potential risks if you are not reviewing your entire business for them.
KEEP HACKERS OUT
Enhancing your cybersecurity is a multifaceted procedure. It encompasses all parts of your system and numerous activities, such as incorporating software and backing up your data.
This makes the process highly complex.
If you need help in ensuring your cybersecurity is as effective as possible, contact Nwaj Tech for a quick 15-minute, obligation-free chat. Let’s talk about how we can help you improve your cybersecurity and keep the bad guys out.
Article used with permission from The Technology Press.








