
Using the NIST CSF to Meet Cybersecurity and Compliance Requirements in Your Small Business
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a set of guidelines, standards, and best practices designed to help organizations manage and reduce cybersecurity risk. The framework is a voluntary framework that can be used by organizations of all sizes, types, and sectors to improve their cybersecurity posture.
In this blog post, we will take a deep dive into the NIST CSF, explaining its key components, benefits, and how to implement it.
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a comprehensive approach to managing cybersecurity risk. It is based on five core functions, which are Identify, Protect, Detect, Respond, and Recover. Each of these functions consists of categories and subcategories that provide a structured and organized approach to managing cybersecurity risk.
The framework is designed to be flexible and customizable, allowing organizations to tailor it to their specific needs and requirements. It is also designed to be scalable, meaning it can be used by organizations of all sizes and sectors, from small businesses to large enterprises.
The 5 core functions of the NIST Cybersecurity Framework explained
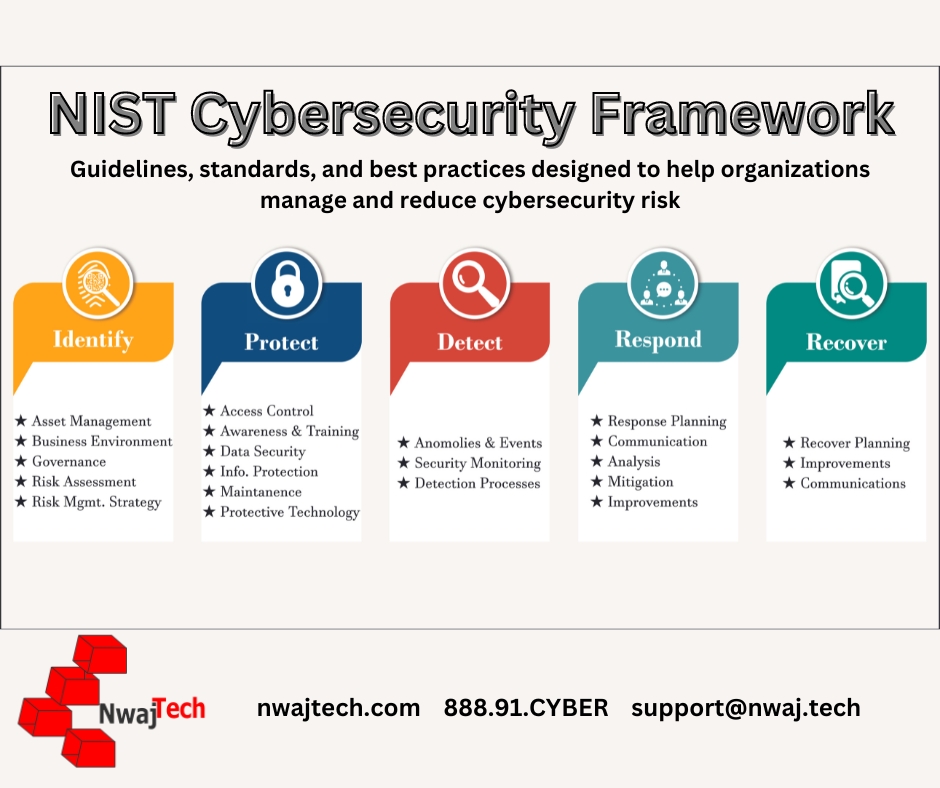 Identify: This section focuses on identifying and understanding the assets, systems, data, and capabilities of the organization that need to be protected. It involves understanding the cybersecurity risks, including threats, vulnerabilities, and potential impacts. The sub-sections are:
Identify: This section focuses on identifying and understanding the assets, systems, data, and capabilities of the organization that need to be protected. It involves understanding the cybersecurity risks, including threats, vulnerabilities, and potential impacts. The sub-sections are:
- Asset Management (ID.AM): The process of identifying and managing the organization’s assets, including hardware, software, data, and personnel.
- Business Environment (ID.BE): The process of understanding the organization’s business environment, including its mission, objectives, stakeholders, and regulatory requirements.
- Governance (ID.GV): The process of establishing and maintaining a framework for managing cybersecurity risk and ensuring that the organization’s cybersecurity program aligns with its overall mission and objectives.
- Risk Assessment (ID.RA): The process of identifying, assessing, and prioritizing cybersecurity risks to the organization’s assets and systems.
- Risk Management Strategy (ID.RM): The process of developing and implementing a strategy for managing cybersecurity risk that is aligned with the organization’s mission, objectives, and risk appetite.
- Protect: This section focuses on putting in place safeguards to protect the identified assets and systems from cyber threats. This includes implementing access controls, providing awareness training, implementing protective technology, and establishing secure configurations. The sub-sections are:
- Access Control (PR.AC): The process of limiting access to the organization’s assets and systems based on the principle of least privilege.
- Awareness and Training (PR.AT): The process of providing training and awareness programs to employees, contractors, and other stakeholders to promote good cybersecurity practices and behaviors.
- Data Security (PR.DS): The process of protecting the organization’s data through measures such as encryption, backup, and retention policies.
- Information Protection Processes and Procedures (PR.IP): The process of developing and implementing policies and procedures for protecting the organization’s information assets.
- Maintenance (PR.MA): The process of ensuring that the organization’s hardware, software, and other assets are maintained and updated to protect against vulnerabilities.
- Detect: This section focuses on detecting cybersecurity incidents as they occur or soon after they occur. This includes putting in place monitoring and detection systems, implementing incident response plans, and conducting vulnerability assessments. The sub-sections are:
- Anomalies and Events (DE.AE): The process of monitoring the organization’s networks and systems for abnormal activity and events.
- Security Continuous Monitoring (DE.CM): The process of continuously monitoring the organization’s networks, systems, and applications for security vulnerabilities and threats.
- Detection Processes (DE.DP): The process of developing and implementing procedures for detecting cybersecurity incidents.
- Response Planning (DE.RP): The process of developing and implementing incident response plans that specify the actions to be taken in the event of a cybersecurity incident.
- Respond: This section focuses on responding to cybersecurity incidents. This includes establishing incident response teams, developing response plans, and testing and reviewing the plans on a regular basis. The sub-sections are:
- Communications (RS.CO): The process of establishing and maintaining effective communication channels with stakeholders, including employees, customers, and partners.
- Analysis (RS.AN): The process of analyzing the cybersecurity incident to determine the scope, nature, and impact of the incident.
- Mitigation (RS.MI): The process of containing and mitigating the impact of the cybersecurity incident.
- Improvements (RS.IM): The process of identifying and implementing improvements to the organization’s cybersecurity program based on lessons learned from the incident.
- Recover: This section focuses on recovering from cybersecurity incidents. This includes restoring systems and data, conducting after-action reviews, and updating incident response plans and recovery strategies based on lessons learned. The sub-sections are:
- Recovery Planning (RC.RP): The process of developing and implementing recovery plans that specify the actions to be taken to restore the organization’s systems and data after a cybersecurity incident.
- Improvements (RC.IM): The process of identifying and implementing improvements to the organization’s recovery plans and procedures based on lessons learned from the incident.
- Communications (RC.CO): The process of establishing and maintaining effective communication channels with stakeholders, including employees, customers, and partners, during the recovery process.
- Disaster Recovery (RC.DR): The process of developing and implementing plans for restoring critical business operations and systems in the event of a disaster.
Key Components of the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is made up of three main components:
- Framework Core
The Framework Core is the heart of the NIST CSF. It consists of the five core functions mentioned above, which are further divided into 23 categories and 108 subcategories. The Framework Core provides a common language and structure for managing cybersecurity risk.
- Framework Implementation Tiers
The Framework Implementation Tiers help organizations determine the level of sophistication and rigor they need to implement the framework effectively. There are four tiers, which range from Partial (Tier 1) to Adaptive (Tier 4). The tiers help organizations understand where they are in terms of cybersecurity risk management and identify areas where they need to improve.
- Framework Profiles
The Framework Profiles help organizations customize the framework to their specific needs and requirements. A Framework Profile is a subset of the Framework Core that is selected by an organization based on its business needs, risk tolerance, and resources. The Framework Profile can be used to identify gaps in the organization’s cybersecurity program and prioritize areas for improvement.
Benefits of the NIST Cybersecurity Framework
The NIST Cybersecurity Framework offers several benefits for organizations, including:
- Improved Cybersecurity Risk Management
The framework provides a structured and organized approach to managing cybersecurity risk. By using the framework, organizations can identify, assess, and prioritize their cybersecurity risks and take appropriate actions to manage those risks effectively.
- Common Language and Structure
The framework provides a common language and structure for managing cybersecurity risk. This makes it easier for organizations to communicate about cybersecurity risks with stakeholders, including executives, board members, and regulators.
- Scalable and Flexible
The framework is scalable and flexible, meaning it can be used by organizations of all sizes and sectors. It can be customized to meet the specific needs and requirements of an organization.
- Enhanced Compliance
The framework can help organizations comply with cybersecurity regulations and standards, including the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS).
 How to Implement the NIST Cybersecurity Framework
How to Implement the NIST Cybersecurity Framework
Implementing the NIST CSF can seem daunting, but it doesn’t have to be. Here are the steps to follow:
- Identify Your Critical Assets and Data
The first step in implementing the NIST Cybersecurity Framework is to identify your critical assets and data. These are the assets and data that are essential to your business operations and require protection.
- Conduct a Risk Assessment
The next step is to conduct a risk assessment to identify and assess cybersecurity risks. This involves identifying threats, vulnerabilities, and impacts associated with your critical assets and data.
- Develop a Framework Profile
Based on the results of the risk assessment, you can develop a Framework Profile that is tailored to your organization’s needs and requirements. The Framework Profile should include the categories and subcategories that are most relevant to your organization’s cybersecurity risks and priorities.
- Create an Action Plan
With your Framework Profile in place, you can create an action plan that outlines the steps you need to take to improve your cybersecurity posture. The action plan should include specific goals, timelines, and responsibilities for each step.
- Implement the Framework
Once you have an action plan in place, you can start implementing the framework. This involves putting in place the policies, procedures, and controls needed to manage your cybersecurity risks effectively.
- Monitor and Review
Finally, it’s important to monitor and review your cybersecurity program regularly. This involves regularly assessing your cybersecurity risks, updating your Framework Profile as needed, and reviewing your action plan to ensure that you are making progress toward your goals.
Conclusion
The NIST CSF is a powerful tool that can help organizations of all sizes and sectors manage their cybersecurity risk effectively. By using the framework, organizations can identify, assess, and prioritize their cybersecurity risks and take appropriate actions to manage those risks. The framework is flexible and scalable, meaning it can be customized to meet the specific needs and requirements of an organization. By implementing the NIST CSF, organizations can improve their cybersecurity posture and enhance their compliance with cybersecurity regulations and standards.
Implementing the NIST CSF in your business or practice will go a long way towards satisfying the requirements under the FTC Safeguards Rule and HIPAA and other compliance and governance rules.


